Happy New Year!
Grateful to everyone who has followed and engaged with my research publication last year! Over the past 12 months, I’ve published 18+ in-depth reports and over 10 mini-articles across social media, diving deep into the most pressing and transformative topics within the cybersecurity industry. Now, I’ve aggregated all those insights into one comprehensive report—a year’s worth of research and analysis, distilled into a single, actionable resource.
Since I’ve recently gained a lot of readers and followers, I thought it would be helpful to every reader if I provided one aggregated report that captures the key themes, takeaways, and trends that resonated most with readers globally last year.
This is your chance to revisit the key stories and breakthroughs of 2024 and prepare for what lies ahead in 2025 (more in my next post). Usually, all the themes that defined 2024 serve as a blueprint for thinking about 2025. Thank you to all the operators and cyber leaders who spoke with me and to the vendors who collaborated along the way.
The aggregated analysis goes in-depth into the following and much more as you read:
The key themes and hottest topics in security operations in 2024
The evolving themes in identity security in 2024
Security for AI/LLM, Data security posture management (DSPM) with vendors like Cyera, and AI-security posture management (AI-SPM).
Cloud security industry, Wiz, key trends and adjacent themes
Analysis of the largest cybersecurity vendors throughout 2024
Many more themes uncovered throughout the rest of the piece
If you’ve ever wondered what these definitions entail and their meaning, please scroll through to find them. I’m committed to delivering the best research this upcoming year and look forward to what the next year will bring. I hope this aggregated resource helps both new and old readers of this publication.
Identity Security
Identity security and management continues to be one of the most important and pressing priorities for security and technology leaders. Throughout 2024, the “hottest” theme was the role of non-human identities. However, I covered a host of other research themes and research pieces across cloud identity governance, privilege access management (PAM), identity security protection, the evolution of identity platforms, and much more, as detailed below.
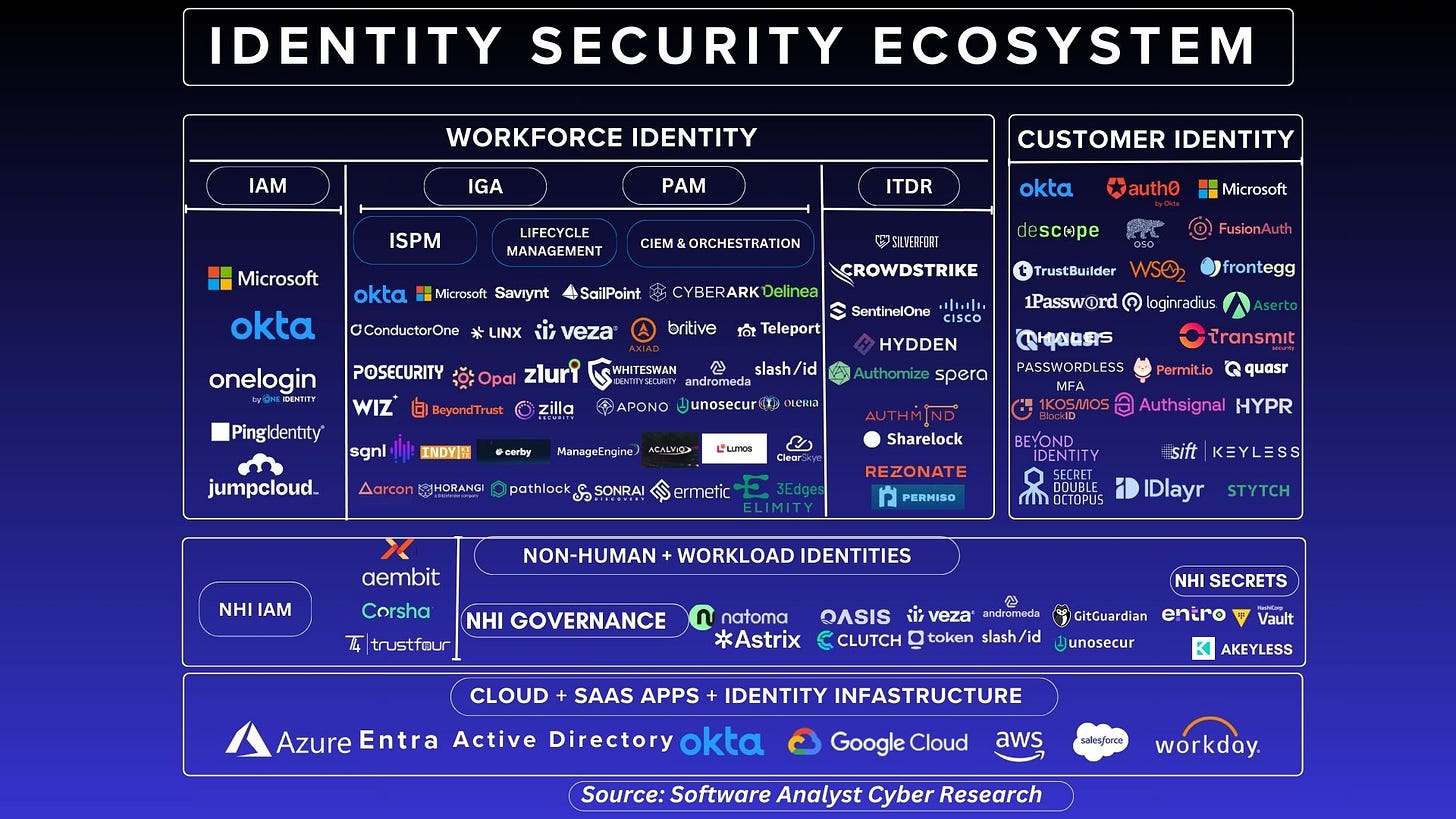
Identity Security Ecosystem (2024)
As of the end of 2024, the market map below makes up around 80% of the value within the identity security ecosystem.
2024 Identity Security Round-up
The identity security ecosystem continues to rapidly evolve. I personally track and have spoken to around 60+ founding teams tracked this year. These vendors are driving innovation in the identity ecosystem. Old ways of doing things are no longer working. Simultaneously, attackers have adapted, prompting a need for new solutions. Based on all the research I conducted last year, a future holistic identity security platform should incorporate at least three of the following:
ITDR+ for identity attack and behavioural protection
Next-gen IGA for SaaS and admin lifecycle management
Centralized real-time engine for all identity data (human + non-human)
Holistic visibility and lifecycle protection of NHIs, including secrets
Identity hygiene and posture management (ISPM) + privilege management
Looking ahead, the key areas to watch in 2025 are:
Non-Human Identities (NHI), Identity Security Posture Management (ISPM), Next-Gen IGA, Advanced ITDR and Identity Protection, and Customer Identity (CIAM). Identity security is at a crossroads; the next big opportunity could emerge from these areas or an entirely new one.
Machine accounts (like automated systems and apps) are rapidly growing within the industry. Companies are using AI to help track and manage bots - to help find, watch, and observe how they behave in the case of an anomaly behaviour.
An identity security platform to solve everything. As depicted on my market map, the industry has many point solutions, and new companies keep getting launched every day. The industry needs a platform that can consolidate key segments of the market. Companies face an important decision: stick with many specialized tools that each do one thing really well, or switch to fewer bigger systems that do everything okay but are easier to manage. Most are leaning toward fewer tools to make life simpler. This comes down to making good security product selections and then figuring out how to make them work effectively together as well as convincing senior leadership about its importance. Vendors need to build a cost-effective security strategy that encompasses on-prem, cloud and SaaS. Read the full reflections here.
NHI with platform potential
As discussed, human identity solutions like IAM, IGA, and PAM have dominated our literature on what defined identity platforms, but the realization of how much Non-Human Identities (NHIs) – which now outnumber humans by 10 to 1 — and the rising implications of AI and AI agents, have sparked increasing interest in NHI broadly.
Key questions atop practitioner’s mind:
Will NHIs become a more significant identity security threat than humans - potentially becoming a platform in their own right?
Will identity security converge, managing human and non-human identities within one stack, or will they always remain distinct?
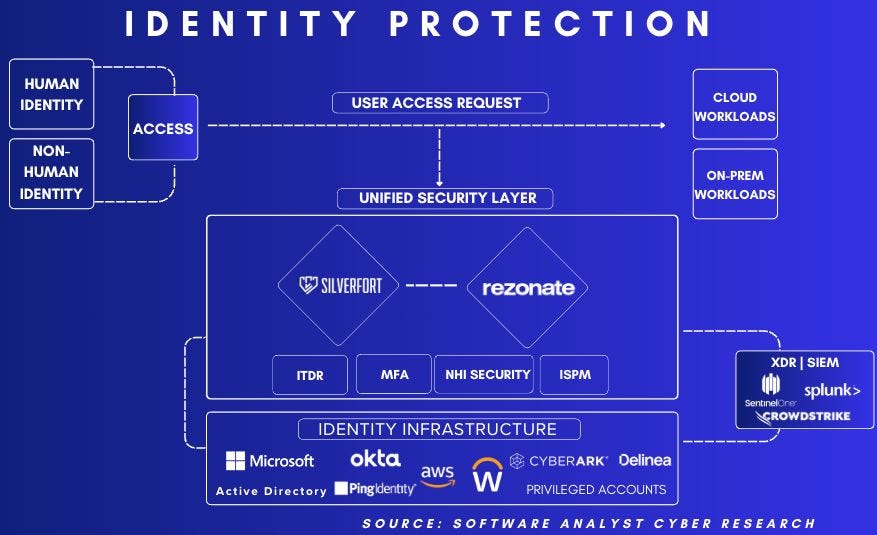
The Role of Identity Security Protection
The second major theme last year in my work was around the role of protecting identities; Identity Detection and Response (ITDR) in a runtime environment is gaining traction as Identity remains one of the #1 attack vectors for cloud-native organizations, driven by AI advancements.
The second major theme in my work last year was the role of protecting identities. Identity Detection and Response (ITDR) in a runtime environment is gaining traction as identity continues to be one of the #1 attack vectors for cloud-native organizations, driven by advancements in AI.
Organizations have realized the loopholes of IAM and MFA authentication security controls to secure all identities within the enterprise. These days, attackers are able to log in successfully after stealing user credentials. Therefore, companies are adopting more identity security controls like ITDR+ to detect anomalous behaviour to protect against cases when an attacker gains access to a network using leaked credentials, or privilege escalations. In the depiction below and this full post using Silverfort as a case study, I break down the importance of this approach. Also, readers should know that my first report in 2025 will cover this theme in-depth.
—
Cloud Identity Governance and platforms
The first identity research report of last year was done in collaboration with Alex Krongold of SentinelOne Ventures and Daniel Bartus at Felicis. We covered the revolving role of workspace identity governance solutions. We distilled down the significant pillars of identity security platforms across:
Authentication (led by Microsoft Security and Okta)
Identity Governance and Administration (led by SailPoint)
Privileged Access Management (led by CyberArk)
We flagged a number of emerging solutions, including P0 Security, Veza, ConductorOne, and Opal Security. As the market evolved throughout the year, we’ve met new solutions which I’ll be covering in 2025. Our core thesis is that a new platform is emerging. As more enterprises move to the cloud and a proliferation of SaaS Apps continues to raise visibility concerns into digital identities, we developed another way of looking at what an anticipated future identity platform might resemble:
Visibility/Posture Management
Authentication/Validation
Lifecycle Management (IGA + PAM + CIEM)
Analytics/Intelligence Layer
Identity Detection & Response (ITDR)
See the full report and analysis.
Other key themes worth tracking within identity in 2025 include Identity Risk Management (IdRM), which combines Identity Posture Management (ISPM) and Identity Threat Detection and Response (ITDR). I highlighted vendors such as Axiad Security that depict this intersection best. I will be writing more on this topic in the new year, but in the meantime, I gave a teaser into this piece, which you can read more about here.
—
Deep-dive guide into Non-Human Identities
NHIs dominated the conversations around identity throughout primarily because of the emergence of many new companies from stealth, but also due to the anticipation of the role that AI will play in helping us understand the importance of NHIs.
Historically, the focus on identity has primarily been on managing human access (IGA), governance (IGA), and privileged accounts (PAM). NHIs aren't new, but they're fragmented across the tech stack. Nearly every leader acknowledges this as an attack vector and that they have limited visibility and control into them. This has led to further funding for these companies.
Additionally, several new companies have emerged due to recent attacks exploiting NHIs (1 every month over the past 13 months) ~ namely the Cloudflare, Snowflake, HuggingFace & AWS attacks, bringing a spotlight to the fact that this area deserves attention. Finally, no single solution has solved the problem - existing large identity companies in IAM, IGA, PAM, ITDR, and CIEM provide only partial visibility into NHIs. This gap has led to the rise of new NHI-focused companies. See my complete analysis and report below:
More Francis NHI resources
I had the opportunity to give a presentation on NHIs in New York with Astrix Security. Please visit to see the full presentation on NHIs. Additionally, I gave another in-depth presentation at the Veza NHI conference here.
See my full report below that goes into depth on NHI, explaining the core concepts, the challenges leading to the rise of these companies, and the future.
—
Does NHI have platform potential?
As discussed, human identity solutions like IAM, IGA, and PAM have dominated our literature on what defined identity platforms, but the realization of how much non-human identities (NHIs) – now outnumber humans by 10 to 1 — and the increasing implications of AI and AI agents has sparked an interested in NHI broadly. Key questions atop practitioner’s mind:
Will NHIs become a more significant identity security threat than humans - that it becomes possible to become a large platform of its own?
Will identity security converge, managing human and non-human identities in one stack, or will they always remain distinct?
I’ll be writing much more on the identity security theme throughout the year. Please ensure to follow-along and be kept abreast.
Security Operations (SOC) Market
The security operations center continues to be a fascinating market. Switching gears to this category, we see a different set of themes dominating conversations throughout the year. A few key themes include understanding the role of AI and its impact on the SOC. This translates to discussions around AI agents and automation. We also saw the role of platformization from the more prominent vendors dominating the conversation throughout 2024. However, I researched and extensively wrote on the following topics below:
Round up of SecOps 2024
Introducing SOC platform
Breakdown of the SOC
The role of AI SOC automation (Pt 1-2)
Francis Hunters’ SOC conference
—
Round up of SecOps 2024
Many key developments occurred last year. In this detailed post, I outline some of the key developments that happened within security operations last year.
I’ve further refined my thesis that the security operations landscape in 2024 revolves around three main tiers:
Data Ingest Layer
Storage, Detection, and Analytics Layer
AI-augmented Response and Decision Layer
The vendor landscape continued to expand. The dominant SOC platforms in security data (MELTs) continue to be Splunk, Google Chronicle, and Microsoft, with competitors like Devo, Exabeam, and Securonix falling behind. CrowdStrike and Palo Alto Networks are gaining traction, broadly speaking, across the market. As seen below, the market ecosystem is still largely fragmented, with many individual vendors across different parts of the ecosystem.
The Biggest Challenges in the modern SOC
Further refining my research, I discovered that the major challenge in the SOC should be data. We need to address reducing data storage costs and improving analyst experience, especially in detection engineering and the triage-to-investigation process. While AI and agents are a focus, the underlying issue remains data quality and management. As data sources increase, the costs and noise in SIEMs rise. Addressing data at the source—through filtering, normalization, threat intel enrichment, and improved detection rules—can reduce false positives, lower analyst workload, and cut storage costs. Solving the data problem could be key to replacing dominant platforms like Splunk. The next big shift in SOC will come from platforms that streamline data and analyst workflows while reducing reliance on legacy tools. Please read my full analysis and breakdown here.
Deep Dive into Next-Gen SIEMs & SOC data platforms
My first report of the year focused on outlining the core elements and structure of the modern SOC. The next evolution of cloud-native data platforms will resemble the depiction below (depending on the enterprise scale/complexity). It would feature:
Security ETL data orchestrators, like Cribl, Observo AI and Monad
Multi-data SIEM platforms like Anvilogic
Next-gen SIEMs and security data lakes like Panther, Hunters and Sekoia
AI Response & reporting like Torq and Hunters
XDR platforms like Palo Alto Networks and CrowdStrike
See more in the report below. I also wrote extensively about the topic below and further dived into the theme in a detailed LinkedIn post.
—
The Case Against Vendor Consolidation in the SOC
Another controversial theme I dived into last year was the case against vendor consolidation. I wrote multiple times about why I don’t see consolidation in the SOC anytime soon. I suggested a new modular cybersecurity architecture that builds around best-of-breed solutions focused on the three major areas of the SOC with some sample vendors. Additionally, in this post, I go into a lot of depth, covering my argument against vendor consolidation.
Read the complete analysis below to see the logic behind my thesis.
—
SOC automation and next-gen SOAR (part 1)
The topic of how to automate the SOC was the most prominent SOC theme of 2024. I tackled the subject in two different categories. First, I collaborated with Josh Trup. This report was a preliminary breakdown covering the history of automation in the SOC and its core use cases. We further uncovered how we got here with the challenges of the SOC, charting the evolution of SOC automation through the following stages and its future:
Custom, in-house automation scripts
Generalist automation solutions
Security SOAR platforms
AI-hyperautomation platforms
The recent emergence of AI-SOC startups
We wrote extensively about the theme. See the complete analysis below.
—
SOC automation: AI SOC (part 2)
As 2024 continued, the discussion around automation further escalated to further discussion of the role of AI and agentic automation processes throughout the SOC. We began to hear more about the idea of AI-SOC or “fully automated SOC“ - many ideas that I vehemently disagreed with based on the research in my ecosystem.
I collaborated with Filip Stojkovski to delve into the role of AI in the SOC. One of our key takeaways was that the term "AI for SOC" was misleading & the market is better categorized as AI-Augmented SOC Analysts or AI-SOC Assistants, focusing on augmenting and enhancing human workflows rather than replacing analysts entirely. Another key takeaway is that many CISOs and analysts remain skeptical about putting AI in the driver's seat/on the front lines in today’s market, preferring tools that enhance workflows without replacing roles. This report categorizes the market into four types of solutions:
AI-XDR & Security Co-Pilot Platforms
AI-SOC Tier 1 Analyst solutions
AI-SOC Tier 2/3 Analyst solutions
AI Automation Engineers
Read our complete analysis in the report below to see more insights on what we uncovered:
In the near term, next-gen SOAR solutions combined with AI and LLMs represent the most promising direction. These tools build upon existing playbooks while enhancing their usability, helping SOC teams address alert fatigue, reduce costs, and improve response times. I elaborated on this further in this LinkedIn post. Longer term, it will be interesting to see how AI truly changes the modern SOC.
—
Key SOC Online Contributions
Beyond just writing and analysis, I present my thesis on the market, like the SOC, through presentations, forewords and guest speaker engagements.
Automation Webinar: Torq recently published one of the best manifestos for any company considering integrating AI within their SOC. I found the guide very practical, with live attack examples and addressing key concerns like transparency and human oversight. SOC leaders still face limitations with traditional SOAR platforms, but new AI automation solutions like Torq show real results. Please see the full resource on AI in the SOC. Additionally, I gave an interview with Torq discussing AI & SOC automation, and I gave the forward for this manifesto on AI-SOC. I highly recommend it for reading.
Hunters Conference: I presented my ideas at Hunters security conference, a large virtual conference for SOC professionals. You’ll walk away with threat-hunting best practices, an insider’s perspective on SOC best practices, and a look into the future of Hunters and SecOps. At the Conference, I shared my vision for the future of SOCs based on my research this year - diving into all three model SOC layers and evaluating the case for best of breed vs platforms within the SOC. You can watch my presentation here, as well read some of my detailed post outlining the SOC architecture for the future.
Data Security & AI/LLM Security
Data is foundational to the success of enterprise adoption of AI/LLM. Throughout 2024, I wrote about the following topics:
Security for AI/LLMs
Data security platforms
The role of AI-SPM
—
Data Security Platforms
With increasing data regulatory frameworks globally, ransomware has emerged as the #1 attack vector costing organizations millions, and the rise of Gen-AI adoption (while data being the 🔑 for AI). This category has seen the largest volume of acquisitions - I outlined many of them in this post. Altitude Cyber funding data shows over $10B worth of investment and over 574+ funding activities across all categories of data security between 2020-2024! All signs point to data security and governance as the building blocks for enterprise AI. I published an in-depth research report on how the next data security platform will evolve and key areas that will drive the next $1B+ data platform:
DSPM – Discover and classify sensitive data
DLP – Protect data where it’s accessed (in transit and at rest)
Data Recovery – Restore lost or encrypted data
AI/LLM Security – Secure data used in AI/LLM models
I explain how organizations can build a robust data strategy to secure their data—from visibility to protection and recovery—across on-prem, SaaS, and cloud environments. I highlight the key vendors and platforms. As for the LinkedIn post: See additional thoughts and short form pieces around Cyera’s data security conference highlights, as well as the thesis for data security. See the complete report below:
—
Data Security Acquisitions
Altitude cyber funding data reveals $10B+ in investments and 574+ funding activities in data security between 2020-2024. The rate of acquisitions within data security is fascinating to watch.
The major activity across the space includes Palo Alto Networks acquiring Dig Security (2023), Rubrik acquiring Laminar (2023), CrowdStrike acquiring Flow (2024), Proofpoint acquiring Normalyze (2024), Netskope acquiring Dasera (2024), Fortinet acquiring Next DLP (2024), Tenable acquiring Eureka (2024), Cyera acquiring Trail Security (2024), Zscaler building out their solution internally, and Salesforce acquiring Own Company (2024). The rapid pace of acquisitions indicates a clear demand for data security and points to broader market consolidation. It also shows that companies are racing to enhance data protection capabilities amid the AI boom. For more context on my thoughts, read more about the acquisitions here.
Security for AI/LLM
Security for AI/LLM emerged as a major theme in 2024, as organizations widely adopted GenAI. Companies shifted from outright banning GenAI to thoughtfully evaluating how to leverage AI securely for their benefit. Enterprises focused on protecting against critical risks—particularly the disclosure of sensitive data and PII through GenAI systems. Two other pressing concerns were prompt injection (where AI prompts are manipulated to extract or insert malicious information) and shadow AI (unauthorized AI use that goes undetected).
As closed-source models like ChatGPT and Anthropic continued to gain market share, we are seeing companies seeking to secure GenAI usage across enterprises by addressing the risks associated with tools like ChatGPT, Microsoft 365 Copilot, and custom AI integrations.
I partnered with Zain Rizavi, a top investor at Ridge Ventures, to compile a comprehensive analysis and report on the ecosystem, including the key vendors to watch across the space.
One of the core analogies we used across the report was discussing how major platform shifts have occurred across cybersecurity. One close analogy is the evolution of cloud architecture relative to cloud security (new architecture, new security solutions), which has evolved over multiple generations (think Redlock, Orca, to Wiz). It took a long time and multiple years to see the most successful cybersecurity vendor secure this architecture. The AI security market will likely follow a similar trajectory. 2025 will reveal the winners, as we can expect CISOs to start allocating toward these AI projects. I provide brief commentary within this AI/LLM LinkedIn post. As for the report, please see the full analysis below:
__
Securing of cloud centric AI-Models (AI-SPM)
I’ll keep this one short, but AI-SPM was a core theme that evolved through last year. To level set, AI-Security posture Management (SPM) technologies are designed to secure AI models, pipelines, data, and services within production environments (slightly different from AI security startups scanning the models themselves). AI-SPM helps with understanding the types of AI models in prod, setting configuration controls and ensuring that AI systems are deployed securely and compliant.
The reality is that AI-SPM builds upon existing CSPM (scanning for cloud misconfigurations), DSPM (understanding context and sensitivity of data relative to compliance), and CIEM (managing cloud identities and entitlements), but with the end goal of addressing the challenges of AI deployments in prod. For the adjacent market categories to the securing of AI/LLMs, please see this analysis below that delves deeper into the role of AI-SPM. I had a detailed post in this LinkedIn report.
The Cloud Security Industry
The Growth of Cloud-Native Application Protection Platforms (CNAPP)
In an era where digital transformation is no longer a choice but a mandate, the cloud has become the backbone of modern business. Yet, as organizations migrate their most critical operations and sensitive data to the cloud, the attack surface expands exponentially. The question is no longer whether to secure the cloud but how to stay ahead in a race where the stakes are everything. Cloud security continued to experience rapid growth throughout the last year.
One of the proudest deep dives, collaborations and longest report I participated in last year was working with . The evolution of cloud security vendors over the past decade, from the emphasis on visibility to runtime protection has been fascinating to watch. We provide an exhaustive and in-depth analysis of over 10+ major cloud security vendors. In the report, we provide a framework for understanding cloud security: Posture and Runtime. We explore how adjacent markets fit in, discuss CNAPP’s limitations, and propose key questions to determine its future.
See the complete analysis below:
—
Competitive landscape: Wiz outlasts cloud security competitors
As a general observation, it's pretty remarkable to see how this market is still growing despite being 10-14 years into the cloud journey. The future battle in this market will be to win the Runtime, ASPM, and SOC components of the cloud. Below, I shared a short tidbit on the rise of Wiz’s cloud security business, including some context here.
—
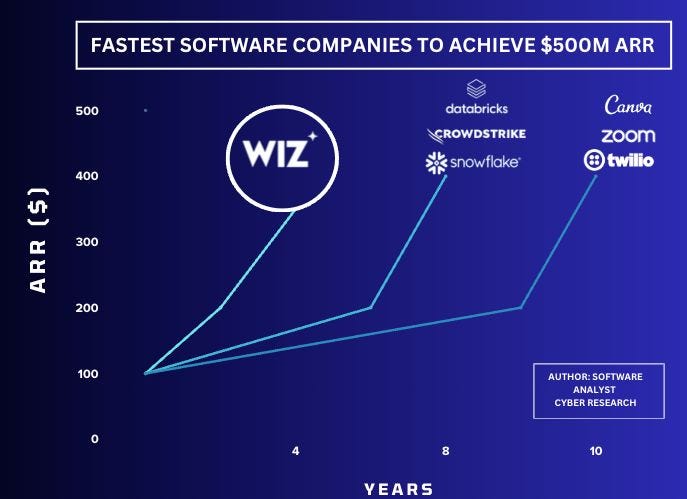
How Wiz became the fastest-growing software company to hit $500M
Wiz was the fastest-growing company to reach $500M in just four years, and if it can sustain a fraction of this growth, it’s poised to hit $1B next year—an achievement only a few companies like OpenAI can match. Having previously co-authored an extensive report on CNAPP and the evolution of Palo Alto Networks under Nikesh last year, I felt compelled to dive deeper into the Wiz product architecture, GTM & founding team dynamics that have led to Wiz’s remarkable growth. This report went deep into Wiz’s evolution through three key stages:
The report uncovered:
Wiz 1.0: The foundational role of the Wiz graph in shaping their agentless scanning and early user experience.
Wiz 2.0: Integrating code and runtime context to building a cloud platform.
Wiz 3.0: The roadmap to $1B, new growth areas and competition.
See the full complete analysis below:
—
Cloud Security and the role of runtime analysis (Wiz's release of Defend)
As discussed earlier, the emphasis on cloud security has evolved away from pure scanning and visibility (traditionally known as CSPM), and increasingly shifted to the importance of runtime analysis and context. Similarly, Wiz needed to move beyond agentless CSPM scanning to become a complete left-to-right cloud security platform. With Wiz Defend, they are closing that gap, addressing cloud security’s runtime protection challenge.
Wiz Defend, a cloud detection and response (CDR) solution, helps detect, investigate, and respond to runtime threats. As aided by its initial acquisition of Gem security, it strengthens cloud monitoring and investigation workflows for better remediation. This will be hugely valuable for SOC teams that struggle with cloud logs and vulnerabilities. I wrote about the announcement and its implications in this detailed post.
Application Security
Earlier in the year, I wrote extensively on different application security topics and themes related to current market development. I tackled the following topics:
Deep-dive into cloud and app sec
Software supply chain
ASPM - Part 1 and 2
Introduction to Application Security
If you’ve ever looked for an introductory piece to app security, my piece below explains the industry in depth. Application Security refers to the practice of protecting software applications from security threats and vulnerabilities throughout an application’s lifecycle—from development to deployment. Many sub-sectors have evolved within this space. My piece primarily segments the landscape into six areas:
AST Solutions (SAST, DAST, IaC)
Software Supply Chain (SCA)
Cloud Security Vendors (CNAPP)
SaaS Security (SSPM/CASB)
Vulnerability Management (VMs)
Runtime Security (WAF, RASP, APIs)
See the complete analysis below:
—
Application Security Posture Management (ASPM)
The biggest theme that dominated the conversations on the vendor side within application security in 2024 was Application Security Posture Management (ASPM). Its core notion is around giving organizations visibility into all of all their applications, its components and how they’re configured with the ultimate goal of identifying, managing, and importantly, reducing risks in their applications throughout the development and deployment process. Instead of overwhelming security teams with all possible issues, ASPM focuses on identifying the most critical risks that could lead to a security breach. Below, I partnered up with to dive into this market space. See the complete analysis below. We highlighted solutions like ArmorCode, Cycode, and Snyk. We also see emerging app sec vendors like Xygeni, Staklok, Scribe - E2E Software Supply Chain Security, Aikido, OX Security, Backlash, and Arnica.
To see more of the nuanced and LinkedIn perspective on the topic, please read more on Wiz ASPM Report.
—
Software Supply Chain Report
Another hot theme that emerged in 2022 and 2023 was the topic of software supply chain security to secure the use of open-source libraries and packages. I put together a deep-dive report on the software supply chain security ecosystem in collaboration with Nipun Gupta. This is a follow-up to my cloud and application security research piece. Last year, when I collaborated with Clint Gibler, we provided an overview of the software supply chain category and some leading vendors. In this new piece, we wanted to elaborate on recent developments in SSCS, newer approaches, and regulations. This market category of cybersecurity is becoming saturated, with many vendors’ offerings.
The second report went into another level of depth below:
Company Reports - Public Cyber Companies
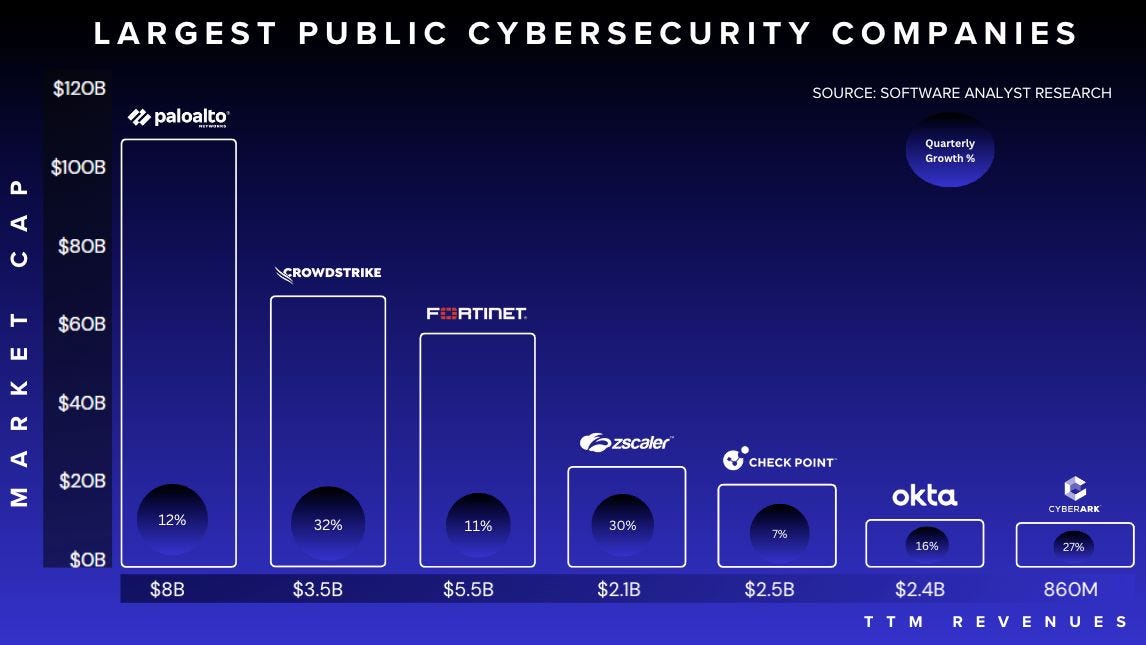
Throughout last year, I would generally provide a quarterly analysis of the largest cyber companies globally. As we know, the cybersecurity industry has over 4000 vendors and $200B+ in enterprise spending, yet:
Fewer than <20 companies drive 65% of that spending
Only <7 public companies are over a $10B market cap
The largest vendor holds only a 9% market share
Generally, I would provide general data points around the top 5 "pureplay" vendors leading the charge: Palo Alto Networks, CrowdStrike, Fortinet, Zscaler, Okta and CyberArk.
Here are some quarterly reviews:
Market review Q3 2024 summary: See the complete analysis below
Market review Q1 & Q2 2024 summary: See the complete analysis below and some online commentary on a few vendors.
Palo Alto Networks Platformization
I provide some short-form analysis and content around the large platforms.
Interviews and Speaking Engagements
Occasionally, I hosted several webinars. One of them was hosting with Ivana Spears. We discuss the top cybersecurity companies, the current thesis, and the tailwinds driving these key cybersecurity players over the next 3-5 years. See the entire webinar here.
I hosted another webinar about cybersecurity with a few security leaders and practitioners. I shared some themes and reflections around the Blackhat cybersecurity conference. I discussed how identity is becoming a central theme and the state of cyber.
Additionally, I gave an interview with the Founder and CEO at ConductorOne; the discussion uncovered a wide host of topics, including one of them being How to Think About Non-Human Identities and AI.
Other topics & categories
Plans for 2025
Thank you to everyone who engaged, read my work and shared it throughout 2024. While I have no clue what 2025 holds, I’m looking forward to continuing to share in-depth and research-backed analysis with the larger community. I will be sharing more in an upcoming post on what readers can expect to see this year.
Bootcamp Waitlist (if interested)
A few times throughout 2024, I hosted a cybersecurity bootcamp with some renowned CISOs and security leaders that introduced participants to the cybersecurity industry broadly. My bootcamp provides a deep dive into all the different categories and sectors I cover across cybersecurity. It specifically focuses on the Identity Security industry, Security Operations (SOC), data/AI security, and Cloud and Application security. The bootcamp provides a complete summary of how to triangulate across all sectors. I’ll be launching more details about the re-branded course, later this year. See more information below if you’d like to sign up for the waitlist or check it out.
Stay tuned for future announcements and developments!
Thank you very much!